15 เว็บแทงบอลออนไลน์ กำไรสูงที่สุดในไทย ปี 2025
ในบทความนี้เรามาพูดถึงเกมบอลออนไลน์ที่น่าสนใจกัน เน้นไปที่เครดิตฟรีและเว็บไซต์ที่เป็น เว็บตรง ไม่ต้องผ่านเอเย่นต์ เราได้รวบรวมเกมเดิมพันการพนันฟุตบอล ครบวงจร มาให้คุณแล้วที่นี่ แต่ละเว็บเดิมพัน ผู้เล่นจะพบกับตัวเลือกรูปแบบเกมที่หลากหลาย สามารถเลือกเล่นได้ตามใจชอบมากมาย
รับรองได้เลยว่า ผู้เล่นจะสามารถสร้างกำไรมูลค่าสูงสุดได้ถึง 1 ล้านบาทด้วยกัน ไม่ว่าจะเป็นรูปแบบเกมพนันบอลแบบไหนก็ตามเช่น แทงบอลเต็ง, แทงบอลเสต็ป, แทงบอลแบบ 1×2, แทงบอลสูงต่ำ, และแทงบอลแฮนดิแคป รวมถึงตัวเลือกอื่นๆ อีกมากมาย
ผู้เล่นยังสามารถเข้าร่วมการเดิมพันบ้านผลบอลในลีกฟุตบอลทั้งในประเทศไทยและต่างประเทศ เพื่อเพิ่มโอกาสในการได้รับกำไรสูงสุดที่มากถึง 3,000 เท่าของเงินเดิมพันที่คุณวางเดิมพันไว้ ไม่เพียงแค่นั้น เราก็ได้รวบรวมเว็บแทงบอลออนไลน์ ที่มีความน่าเชื่อถือและมาพร้อมกับโปรโมชั่นที่น่าสนใจอีกมากมาย มาแล้วที่นี่ ตามมาอ่านรายละเอียดของแต่ละเว็บเดิมพันกันต่อได้เลย
- ทั้งหมด
โบนัสต้อนรับ 200% เครดิตฟรีสูงสุด 12,500 บาท
โบนัสต้อนรับ 200% เครดิตฟรีสูงสุด 12,500 บาท
- โบนัสยืนยันเบอร์โทรศัพท์ 100 บาท
- ฝากเงินได้หลายวิธีการ
- เชื่อถือได้ การเงินมั่นคง และมีชื่อเสียงระดับโลก
โบนัสสมาชิกใหม่ 100% สูงสุด 5,000 บาท
โบนัสสมาชิกใหม่ 100% สูงสุด 5,000 บาท
- อัตราต่อรองและโบนัสสำหรับการพนันกีฬาที่น่าตื่นตาตื่นใจ
- เกมคาสิโนออนไลน์ที่น่าตื่นเต้นหลากหลายเกม
- โปรโมชันพิเศษเฉพาะสำหรับผู้เล่นชาวไทย
โบนัสต้อนรับสุดพิเศษ 150% + 50 ฟรีสปิน!
โบนัสต้อนรับสุดพิเศษ 150% + 50 ฟรีสปิน!
- ยืนยันโปรไฟล์ รับฟรี 60 บาท ทันที
- ชวนเพื่อน รับโบนัสสูงสุด 12,000 บาทต่อสัปดาห์!
- รับเงินคืนรายวัน 1.2% ไม่จำกัด – ถอนได้ไม่อั้น
โบนัสสมาชิกใหม่ 120% สูงสุด 6,000 บาท
โบนัสสมาชิกใหม่ 120% สูงสุด 6,000 บาท
- ภารกิจเช็คอินรายวันรับสูงสุด 18,888 บาท
- เครดิตฟรีสูงสุด 25,555 บาททุกวัน
- โบนัสพิเศษรายเดือนสูงสุด 38,888 บาทสำหรับสมาชิก VIP
- แลกรับของขวัญพรีเมียมใน U-Mall

โบนัสสมาชิกใหม่ 300% สูงสุด 9,000 บาท
โบนัสสมาชิกใหม่ 300% สูงสุด 9,000 บาท
- เล่นเกมคาสิโนสดออนไลน์กับเว็บพนันออนไลน์ที่ดีที่สุด
- โบนัสต้อนรับสำหรับแฟนตัวยงคาสิโนและสล็อตสูงสุด 8,000 บาท
- MS.Slot - คาสิโนออนไลน์ที่ดีที่สุดในประเทศไทย

ฝากครั้งแรกรับโบนัส 100% สูงสุด 888 บาท ฝากขั้นต่ำเพียง 1 บาท
ฝากครั้งแรกรับโบนัส 100% สูงสุด 888 บาท ฝากขั้นต่ำเพียง 1 บาท
- ระบบฝากเงินอัตโนมัติ
- ฝากขั้นต่ำเพียง 1 บาท
- มีค่ายเกมให้เลือกหลากหลาย PG ลิขสิทธิ์แท้
รับฟรี 666 ทุกวัน! สำหรับกีฬาและคาสิโน
รับฟรี 666 ทุกวัน! สำหรับกีฬาและคาสิโน
- โบนัสเงินฝาก 100% สุดสัปดาห์ สำหรับสล็อต!
- ระบบฝากถอนอัตโนมัติ
- มีแอพมือถือให้บริการ

88% คาสิโนสด โบนัสต้อนรับพิเศษ
88% คาสิโนสด โบนัสต้อนรับพิเศษ
- สปอร์ตบุ๊คออนไลน์ที่มีชื่อเสียงและเป็นที่ยอมรับทั่วโลก
- การจ่ายเงินที่รวดเร็ว พร้อมทีมสนับสนุนลูกค้าที่ตอบสนองไวทุกคำถาม
- หลากหลายโปรดักส์ พร้อมโปรโมชั่นที่ออกแบบมาเฉพาะสำหรับคุณ
โบนัสต้อนรับสมาชิกใหม่ 30% สำหรับสล็อต
โบนัสต้อนรับสมาชิกใหม่ 30% สำหรับสล็อต
- โบนัสต้อนรับสล็อต 100% เครดิตฟรีสูงสุด 2,000 บาท
- สมัครสมาชิกวันนี้ลุ้นโบนัสลึกลับ 250 บาท
- โบนัสฝากเงินครั้งแรกของวันสูงสุด 5,000 บาท
- โบนัสชวนเพื่อน 191 บาท + ภารกิจสะสมรับโบนัสสูงสุด 188,888 บาท
- โบนัสคืนเงิน VIP รายสัปดาห์สูงสุด 5,888 บาท

ต้อนรับสายคาสิโน! รับ 855 ฟรีทุกวัน สำหรับการเดิมพันครั้งแรกของคุณ
ต้อนรับสายคาสิโน! รับ 855 ฟรีทุกวัน สำหรับการเดิมพันครั้งแรกของคุณ
- ทุกบิลเดิมพันรับเงินคืนคาสิโน 100%
- เล่นสล็อต เราจ่ายคืน 100%
- GOD855 ฝากขั้นต่ำเพียง 10 บาทเท่านั้น

เกมหลากหลายครบทุกแนว พร้อมโปรโมชั่นสุดพิเศษเฉพาะคนไทย
เกมหลากหลายครบทุกแนว พร้อมโปรโมชั่นสุดพิเศษเฉพาะคนไทย
- เกมหลากหลายครบทุกแนว พร้อมโปรโมชั่นสุดพิเศษเฉพาะคนไทย
- ผู้สนับสนุนหลักในกีฬาระดับโลกหลายรายการ แพลตฟอร์มที่น่าเชื่อถือที่สุดตั้งแต่ปี 2007
- ฝากถอนรวดเร็ว บริการลูกค้าโดยทีมงานคนไทยโดยเฉพาะ
โบนัสเงินฝาก 100% + ฟรีสปิน 150 ครั้ง
โบนัสเงินฝาก 100% + ฟรีสปิน 150 ครั้ง
- ร่วมโปรแกรมแนะนำเพื่อน รับรายได้สุดคุ้ม
- สปอร์ตบุ๊ก & พันธมิตรการเดิมพันอย่างเป็นทางการของ UFC เอเชีย
- ครบทุกความบันเทิงกับคาสิโนกว่า 9,000 เกม

โบนัสฝากแรก 150% สูงสุด 5,000 บาท
โบนัสฝากแรก 150% สูงสุด 5,000 บาท
- ทุกยอดเดิมพันคืนสูงสุด 1%
- คืนยอดเสียสูงสุด 12%
- แจกพอยด์ทุกเดิมพันหรือทำเควสรับต่อสอง แลกเงินและของลักซูรีฟรี
- ฝาก-ถอนรวดเร็วด้วย QR & True Money
- ระบบ VIP แจกโบนัสวันเกิด โบนัสอัพเกรด % คืนเงินสูงสุด
รับโบนัสต้อนรับสูงสุดถึง ฿16,000!
รับโบนัสต้อนรับสูงสุดถึง ฿16,000!
- แค่สมัครก็รับฟรีสปิน 150 ครั้ง มูลค่าประมาณ ฿500 ไปเลย♪
- คาสิโนออนไลน์อันดับ 1 จากญี่ปุ่น เปิดให้บริการในไทยแล้วอย่างเป็นทางการ!
- สนุกกับเกมฟรีรายวันทัวร์นาเมนต์ และแคมเปญแจกหนักแบบจัดเต็มทุกวัน★
โบนัสต้อนรับ 288% สูงสุดถึง 21,600 THB
โบนัสต้อนรับ 288% สูงสุดถึง 21,600 THB
- เกมที่ดีที่สุดจาก Pragmatic, Jili Games , PG Soft และอีกมากมาย
- เงินคืนสูงถึง 0.7% รายสัปดาห์
- ตัวเลือกการชำระเงินยอดนิยมรวมถึง crypto
โบนัสฝากเงินครั้งแรก 100% สูงสุด 5,200 บาท
โบนัสฝากเงินครั้งแรก 100% สูงสุด 5,200 บาท
- เกมสล็อตออนไลน์ที่ได้รับการคัดเลือกโดยเฉพาะ
- โบนัสต้อนรับก้อนโต
- เกมคาสิโนออนไลน์ยอดนิยม

แพ็กเกจต้อนรับสูงสุด €1,000 + ฟรีสปิน 100 ครั้ง
แพ็กเกจต้อนรับสูงสุด €1,000 + ฟรีสปิน 100 ครั้ง
- รองรับการชำระเงินผ่าน Apple Pay
- เกมคาสิโนสดที่ดีที่สุดจาก Pragmatic และ Evolution
- มีเกมมากกว่า 2,000 เกมจากค่ายเกมชั้นนำทั้งหมด
โบนัส 200% สูงสุดถึง €5000 + 50 ฟรีสปิน + 10% แคชแบ็กรายสัปดาห์
โบนัส 200% สูงสุดถึง €5000 + 50 ฟรีสปิน + 10% แคชแบ็กรายสัปดาห์
- ฝาก-ถอนรวดเร็วและปลอดภัย
- มีแอปมือถือให้ใช้งาน
- มีเกมคาสิโนให้เลือกเล่นมากมาย
โบนัสฝากเงินครั้งแรก 200% สูงสุด 10 ETH
โบนัสฝากเงินครั้งแรก 200% สูงสุด 10 ETH
- คาสิโน Telegram ยอดนิยมอันดับ 1
- คาสิโนที่มีใบอนุญาตและไม่มี KYC
- ฝากและถอนด้วยคริปโตได้
โบนัสต้อนรับ 200% สูงสุด 1 BTC + ฟรีสปิน 50 ครั้ง
โบนัสต้อนรับ 200% สูงสุด 1 BTC + ฟรีสปิน 50 ครั้ง
- คาสิโน Telegram ที่มีใบอนุญาตเว็บไซต์แรกของโลก
- เว็บพนันกีฬา & คาสิโนคริปโตเปิดใหม่
- ไม่ต้องยืนยันอีเมลหรือ KYC
- คาสิโนแบบไม่ต้องเปิดเผยตัวตน
โบนัสคืนเงิน 200% สูงสุด 25,000 USD/ 1 BTC + ฟรีสปิน 10 ครั้ง
โบนัสคืนเงิน 200% สูงสุด 25,000 USD/ 1 BTC + ฟรีสปิน 10 ครั้ง
- เกมพนันออนไลน์ให้เลือกเยอะ
- คาสิโน Telegram ที่ดีที่สุด
- โบนัสต้อนรับมหาศาล
โบนัสต้อนรับ 200% สูงถึง 10,000 USDT คืนเงินรายสัปดาห์ 10%
โบนัสต้อนรับ 200% สูงถึง 10,000 USDT คืนเงินรายสัปดาห์ 10%
- คาสิโนที่ไม่ลงรอยกันที่เพิ่งเปิดตัวพร้อม kyc ที่ง่ายดาย
- บรรยากาศทางสังคมพร้อมเคล็ดลับการเดิมพัน
- เลือกจากสกุลเงินดิจิทัลที่แตกต่างกันเพื่อฝาก
โบนัสฝากเงิน 150% สูงสุด $2,000
โบนัสฝากเงิน 150% สูงสุด $2,000
- คืนเงินโป๊กเกอร์ออนไลน์ 33% ทุกวันจันทร์
- ฝากและถอนเงินด้วยคริปโตแบบไม่มีค่าธรรมเนียม
- เว็บโป๊กเกอร์คริปโตแบบไม่เปิดเผยตัวตนโดยสมบูรณ์และถอนเงินเร็ว
โบนัสคืนเงินรายสัปดาห์ 10% สูงสุด $10,000
โบนัสคืนเงินรายสัปดาห์ 10% สูงสุด $10,000
- สมัครด้วยเบอร์มือถือ
- ขีดจำกัดการเดิมพันสูง & ถอนเงินเร็ว
- ฝากเงินด้วย Visa และ MasterCard

โบนัสฝากเงินครั้งแรก 200% สูงสุด $30,000
โบนัสฝากเงินครั้งแรก 200% สูงสุด $30,000
- โบนัสสูงสุด $100K ต่อสัปดาห์
- ถอนเงินเร็วมาก
- ลูกค้า VIP รับฟรีสปิน เครดิตฟรี และเงินคืนสูงสุด 25%
โบนัสฝากเงินครั้งแรก 200% สูงสุด 5,000 ยูโร
โบนัสฝากเงินครั้งแรก 200% สูงสุด 5,000 ยูโร
- คืนเงิน 10% ต่อสัปดาห์
- เกมคาสิโนและการพนันกีฬาที่น่าตื่นเต้นให้เลือกมากมาย
- ฝากและถอนเงินเร็วและปลอดภัย
โบนัสฝากเงินครั้งแรก 200% สูงสุด 7,500 ยูโร + เงินคืน 10%
โบนัสฝากเงินครั้งแรก 200% สูงสุด 7,500 ยูโร + เงินคืน 10%
- โบนัสต้อนรับก้อนโต
- รองรับคริปโต
- เกมคาสิโนออนไลน์ให้เลือกมากมาย
15 อันดับ แทงบอลออนไลน์ ที่ดีที่สุดในประเทศไทย
- BK8 เว็บแทงบอลออนไลน์ ครบวงจร แจกฟรีเครดิต 3,000 บาท
- UEA8 เล่นพนันบอลออนไลน์ คุ้มที่สุดในประเทศไทย ปี 2025
- We88 เว็บแทงบอลที่ดีที่สุด ขั้นต่ำ 1 บาท ฝาก-ถอน เพียง 30 วินาทีเท่านั้น
- Huc99 เว็บพนันบอล ไม่ผ่านเอเย่นต์ ที่ดีที่สุดในประเทศไทย
- Mama8 – โบนัสต้อนรับ 128% สูงสุด 6,000 บาท, รับเครดิตฟรีพร้อมภารกิจรายวันและ Angpow ฟรี
- Siam855 แทงบอล เริ่มต้น 10 บาท กำไรกว่า 100 เท่าของเงินเดิมพัน
- IB8 เว็บพนันบอล ไม่ผ่านเอเย่นต์ มาตรฐานสากล 100%
- Lucky Block เว็บพนันบอลออนไลน์อันดับหนึ่งที่มองเครดิตสูงสุดถึง 10,000 บาท
- Megadice ให้บริการเดิมพันเกมกีฬาที่รองรับการชำระด้วยคริปโตหลายสกุล
- Me88 เว็บทางเข้า แทงบอล เว็บตรง ไม่ผ่านเอเย่นต์ เงินจริง 100%
- EUBET เว็บพนันบอล ถูกกฎหมาย แจกโบนัส สูงสุด 1,000%
- 77Bet เดิมพัน พนันบอล ได้เงินจริง ราคาดีที่สุดในไทย ปี 2025
- Siam212 เว็บแทงบอลออนไลน์ ขั้นต่ำ 10 บาท ค่าน้ำดีที่สุด แทงบอลได้ทุกคู่
- 22Fun แทงบอลเต็ง ครบวงจร เปิดตลอด 24 ชั่วโมง
- iVip9 เว็บพนัน แทงบอล ครบวงจร เรียลไทม์ เงินจริง ที่ดีที่สุดในไทย
- 88sanook เล่นพนันบอล มือถือ แจกโบนัสสมาชิกใหม่ 1,000 บาทฟรี
BK8 เว็บแทงบอลออนไลน์ ครบวงจร แจกฟรีเครดิต 3,000 บาท
เว็บแทงบอลออนไลน์ BK8 เป็นเว็บไซต์ที่ครบวงจรและยังมีการแจกฟรีเครดิตให้ถึง 3,000 บาท ที่จะทำให้คุณได้สัมผัสประสบการณ์การเดิมพันอย่างครบถ้วน เว็บไซต์นี้ได้รับความน่าเชื่อถือและมีใบอนุญาตจาก First Cagayan Leisure และ Sports Bookie Online Inc ที่มาจากประเทศฟิลิปปินส์ เว็บไซต์นี้ยังมีระบบอัตราการต่อรองในรูปแบบ European, Hong Kong, Malay, และ Indo ที่สามารถช่วยให้คุณได้ทำการเดิมพันได้อย่างหลากหลาย
BK8 ยังมีการจัดหาข้อมูลสถิติของรายการพนันออนไลน์ให้คุณเข้าถึง สามารถใช้งานได้ทั้งบนคอมพิวเตอร์และโน็ตบุ๊ค และมีทีมเจ้าหน้าที่บริการลูกค้าตลอด 24 ชั่วโมง เมื่อเข้าสู่การแทงบอลใน BK8 คุณจะได้พบกับรูปแบบการเดิมพันแบบอัตราการต่อรองแบบเอเชี่ยนแฮนดิแคป ซึ่งช่วยให้คุณสามารถเฝ้าติดตามการเคลื่อนไหวของการแข่งขันได้ตลอดเวลา ไม่เพียงเท่านั้น เว็บไซต์ยังมีโปรโมชั่นและโบนัสมากมายสำหรับนักเดิมพันที่ต้องการแทงบอลออนไลน์ ทำให้คุณสามารถเลือกใช้ตามความต้องการของคุณได้ตามต้องการ
👍 ข้อดีของเว็บแทงบอลออนไลน์ BK8:
- ความครบวงจร: BK8 เป็นเว็บแทงบอลที่มีความครบวงจร ทั้งการเดิมพันแบบอัตราการต่อรองหลากหลายรูปแบบเช่น European, Hong Kong, Malay, และ Indo และยังมีตัวเลือกเกมพนันอื่นๆ ให้เลือกเล่นอีกมากมาย เพื่อให้ผู้เล่นสามารถพนันตามความชอบได้
- ความน่าเชื่อถือ: BK8 ได้รับใบอนุญาตจาก First Cagayan Leisure และ Sports Bookie Online Inc จากประเทศฟิลิปปินส์ ซึ่งเป็นหน่วยงานที่เชื่อถือได้ในการควบคุมและกำกับดูแลกิจการพนันออนไลน์
- สะดวกและหลากหลาย: ผู้เล่นสามารถเข้าถึงเว็บไซต์และทำการเดิมพันได้ทั้งบนคอมพิวเตอร์และโน็ตบุ๊ค และยังมีโอกาสเลือกใช้บริการเมื่อได้ตั้งแต่ระบบเครือข่ายอินเตอร์เน็ต 4G และ 5G
👎 ข้อเสียของเว็บแทงบอลออนไลน์ BK8:
- ข้อจำกัดในโบนัส: บางครั้งอาจมีเงื่อนไขและข้อกำหนดในการใช้งานโบนัสและเครดิตฟรีที่ผู้เล่นควรทราบและทำความเข้าใจก่อนที่จะนำไปใช้
UEA8 เล่นพนันบอลออนไลน์ คุ้มที่สุดในประเทศไทย ปี 2025
UEA8 เป็นเว็บไซต์ที่เล่นพนันบอลออนไลน์และถือว่าคุ้มค่าที่สุดในประเทศไทยในปี 2025 เว็บไซต์แทงบอลออนไลน์ของ UEA8 เป็นอีกหนึ่งเว็บไซต์ที่กำลังได้รับความนิยมอย่างมากในการเดิมพันในประเทศไทย มีการรับรองและถูกกฎหมายจากองค์กรความปลอดภัย เป็นเว็บพนันที่น่าเชื่อถือและมั่นคงมากที่สุดเว็บไซต์นี้เสนอรูปแบบการนำเสนอการเดิมพันและโปรโมชั่นที่น่าสนใจมากมาย เป็นที่สนใจของผู้เล่นใหม่และเก่า
เว็บไซต์ UEA8 เน้นที่ความมั่นคงและความน่าเชื่อถือ ทำให้ผู้เล่นสามารถเลือกใช้เพื่อการเดิมพันที่ปลอดภัยที่สุด UEA8 ยังเป็นเว็บพนันบอลที่มีราคาบอลที่ดีที่สุดและคุณยังสามารถดูบอลสดของทีมโปรดได้ตามต้องการ เว็บแทงบอลนี้ยังเปิดรับสมัครสมาชิกทุกคนและยังมีโอกาสลุ้นรับเงินทุนสองแสนล้านบาท นอกจากนี้เว็บไซต์ยังมีหลากหลายประเภทการเดิมพันออนไลน์ที่ผู้เล่นสามารถเลือกเดิมพันได้ตามต้องการ แล้วยังมีการตั้งราคาต่อรองที่สูงและเป็นทางเลือกที่สามารถนำไปสู่กำไรที่มากขึ้นตามความต้องการของนักเดิมพัน
👍 ข้อดีของ UEA8 เว็บแทงบอลออนไลน์:
- ความมั่นคงและเชื่อถือ: UEA8 เป็นเว็บไซต์ที่ความมั่นคงและเชื่อถือมากที่สุด เนื่องจากได้รับการรับรองจากองค์กรความปลอดภัย และได้รับใบอนุญาตที่ถูกกฎหมาย ทำให้ผู้เล่นสามารถมั่นใจในการทำการเดิมพันออนไลน์
- ราคาบอลที่ดีที่สุด: UEA8 เปิดราคาบอลที่มีความเป็นเอกลักษณ์และดีที่สุด นักเดิมพันจะได้รับราคาที่ถูกต้องและคุ้มค่า เพื่อให้สามารถนำเงินลงเดิมพันและทำกำไรได้ตามความต้องการ
👎 ข้อเสียของ UEA8 เว็บแทงบอลออนไลน์:
- ระบบมือถือยังไม่พร้อม: เว็บแทงบอล UEA8 ยังมีระบบมือถือที่ไม่พร้อมสำหรับนักเดิมพันในตอนนี้ แต่ก็กำลังมีการพัฒนาเพิ่มขึ้น และคาดว่าจะพร้อมใช้งานภายในปลายปีนี้
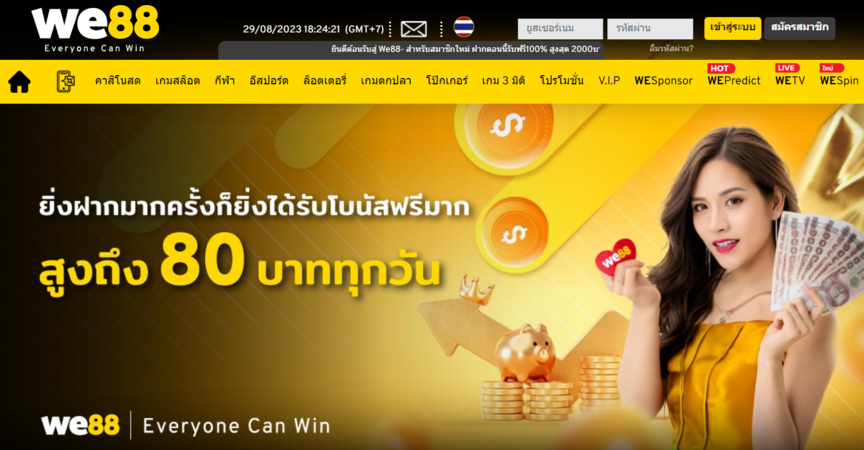
We88 เว็บแทงบอลที่ดีที่สุด ขั้นต่ำ 1 บาท ฝาก-ถอน เพียง 30 วินาที
We88 เป็นเว็บแทงบอลที่ดีที่สุดที่มีขั้นต่ำเพียง 1 บาทในการเดิมพัน และมีบริการฝาก-ถอนเพียงแค่ 30 วินาทีเท่านั้น เว็บแทงบอลออนไลน์ We88 เป็นที่รู้จักในคอมมูนิตี้การเดิมพันกีฬาที่มีทั้งหมดกว่า 90 ชนิดให้คุณเลือกเล่น ไม่ว่าจะเป็นเกมส์แทงบอลที่ได้ความนิยมสูงสุดบนเว็บไซต์ บาสเก็ตบอล เทนนิส กอล์ฟ และอื่นๆ อีกมากมาย รับรองได้เลยว่าครบวงจรแน่นอน
เว็บไซต์นี้เริ่มให้บริการตั้งแต่ปี 2004 และได้รับมาตรฐานความปลอดภัยและความเชื่อถือในการให้บริการ โดยเป็นเว็บไซต์กีฬาออนไลน์ที่มีความเชี่ยวชาญในการนำเสนอการเดิมพันกีฬา หากคุณเป็นสมาชิกของเว็บไซต์นี้ คุณสามารถรับโปรโมชั่นและโบนัสตามต้องการได้ ด้วยการดูแลและบริการจากทางเจ้าหน้าที่และเว็บไซต์เองคุณสามารถเดิมพันออนไลน์ได้ทั้งบนคอมพิวเตอร์ ทุกที่ทุกเวลา พบกับกีฬาฟุตบอลหลายร้อยคู่ต่อวันทั่วโลก ตรวจสอบผลการแข่งขันแบบเรียลไทม์ได้ตลอดเวลา
👍 ข้อดีของ We88 เว็บแทงบอลที่ดีที่สุดที่คุ้มค่า:
- ขั้นต่ำในการเดิมพันเพียง 1 บาท: We88 เป็นที่เชื่อถือของผู้เล่นที่ต้องการเริ่มต้นการเดิมพันอย่างง่าย ด้วยขั้นต่ำเพียง 1 บาทเท่านั้น ผู้เล่นสามารถเข้าร่วมเล่นและลุ้นรับโอกาสทำกำไรได้ง่ายและไม่ซับซ้อน
- ระบบฝาก-ถอนที่รวดเร็วเพียง 30 วินาที: We88 มีระบบฝาก-ถอนที่ทันสมัยและรวดเร็ว ผู้เล่นสามารถทำธุรกรรมการเงินในเวลาไม่ถึง 1 นาที ทำให้ไม่ต้องรอนานในการเข้าถึงเงินที่ได้รับ
- หลากหลายการเดิมพันกีฬา: We88 มีมากกว่า 90 ชนิดของการเดิมพันที่คุณสามารถเลือกเล่น ไม่ว่าจะเป็นเกมส์แทงบอลที่ได้รับความนิยมมากที่สุดบนเว็บไซต์, บาสเก็ตบอล, เทนนิส, กอล์ฟ และอื่นๆ อีกมากมาย
👎 ข้อเสียของ We88 เว็บแทงบอลที่ดีที่สุดที่คุ้มค่า:
- การจำกัดบางประการในการเล่น: อาจมีการจำกัดบางประการในการเล่นหรือเข้าถึงบางส่วนของเว็บไซต์ที่อาจทำให้ผู้เล่นไม่สามารถเล่นเกมหรือใช้บริการบางอย่างได้ตามความต้องการทั้งหมด
Huc99 เว็บพนันบอล ไม่ผ่านเอเย่นต์ ที่ดีที่สุดในประเทศไทย
Huc99 เว็บพนันบอลที่เน้นความไม่ผ่านเอเย่นต์และถือเป็นเว็บไซต์ที่ดีที่สุดในประเทศไทย ที่เน้นการให้บริการทั้งการเดิมพันกีฬาออนไลน์และคาสิโนออนไลน์ นับว่าเป็นตัวเลือกที่ดีสำหรับผู้ที่กำลังมองหาประสบการณ์พนันที่ดีและน่าเชื่อถือ เว็บไซต์ Huc99 มีชื่อเสียงที่ราบรื่นเรื่องการให้บริการคาสิโนออนไลน์และยังเป็นเว็บพนันบอลที่ได้รับความน่าเชื่อถือมากที่สุด นอกจากนี้ ผู้เล่นสามารถที่จะเข้าร่วมการเดิมพันได้ทั้งบนคอมพิวเตอร์และโทรศัพท์มือถือ ทำให้เล่นพนันกับเว็บนี้เป็นเรื่องง่ายและสะดวกสบายมากยิ่งขึ้น
การสมัครสมาชิกบนเว็บไซต์ Huc99 มีหลากหลายรูปแบบให้ผู้เล่นได้เลือกตามความต้องการ ทั้งแบบ VIP และแบบธรรมดา แต่ละรูปแบบก็มีสิทธิประโยชน์และการเดิมพันที่แตกต่างกัน เว็บแทงบอลออนไลน์ Huc99 ยังเป็นพาร์ทเนอร์กับสโมสรเลสเตอร์ ซิตี้ ที่เป็นทีมในพรีเมียร์ลีก เพื่อนำเสนอความสนุกและความตื่นเต้นในการเดิมพันให้กับผู้เล่น นอกจากนี้ยังมีการให้บริการในหลากหลายภาษาและทางเจ้าหน้าที่จะพร้อมช่วยเหลือผู้ใช้งานทั้งภาษาไทยและภาษาอังกฤษตามความต้องการ มีการเริ่มให้บริการตั้งแต่ปี 2007 และได้รับใบอนุญาตจาก PAGCOR First Cagayan ของประเทศฟิลิปปินส์ แสดงให้เห็นถึงความน่าเชื่อถือของเว็บไซต์นี้ สามารถตรวจสอบการใช้งานของเว็บไซต์ได้อย่างง่ายดาย
👍 ข้อดีของ Huc99 เว็บพนันบอล ไม่ผ่านเอเย่นต์:
- เว็บตรง ไม่ผ่านเอเย่นต์: หนึ่งในข้อดีที่สำคัญของ Huc99 คือความโปร่งใสและความน่าเชื่อถือ เนื่องจากเว็บไซต์นี้ไม่ผ่านเอเย่นต์ ทำให้ผู้เล่นมีความมั่นใจในความปลอดภัยและความถูกต้องของการทำการเดิมพัน
- เว็บแทงบอลดีที่สุดในประเทศไทย: Huc99 เป็นเว็บพนันบอลที่ได้รับความยอมรับว่าเป็นที่ดีที่สุดในประเทศไทย นับว่าเป็นตัวเลือกที่น่าสนใจสำหรับผู้ที่ต้องการทดลองเดิมพันและการเล่นพนันที่มีคุณภาพ
- ความหลากหลายในการเดิมพัน: เว็บไซต์นี้มีความหลากหลายในการเดิมพันมากมาย ไม่ว่าจะเป็นการแทงบอล คาสิโน หรือเกมพนันอื่นๆ ผู้เล่นสามารถเลือกเดิมพันตามความชอบได้อย่างหลากหลาย
👎 ข้อเสียของ Huc99 เว็บพนันบอล ไม่ผ่านเอเย่นต์:
- ข้อจำกัดในการเข้าถึงบางประเทศ: บางครั้งอาจมีข้อจำกัดหรือข้อตกลงในการเข้าถึงบางส่วนของเว็บไซต์หรือบริการบางอย่าง ซึ่งอาจทำให้ผู้เล่นต้องทำความเข้าใจและปฏิบัติตามเงื่อนไขเพิ่มเติมเมื่อต้องการใช้บริการในบางรายการหรือส่วนที่จำกัด
Siam855 แทงบอล เริ่มต้น 10 บาท กำไรกว่า 100 เท่าของเงินเดิมพัน
เว็บแทงบอลออนไลน์ Siam855 ด้วยเพียง 10 บาทเท่านั้น และคุณจะได้รับกำไรที่มากกว่า 100 เท่าของยอดเงินเดิมพัน เว็บพนันออนไลน์ Siam855 เป็นที่รู้จักในฐานะเว็บครบวงจรที่นำเสนอตัวเลือกหลากหลายให้แก่ผู้เล่น เข้าเกมแทงบอลที่เรามีทั้งหมด คุณสามารถเข้าเล่นเกมคาสิโนออนไลน์, แทงบอล, พนันกีฬา, สล็อต, บาคาร่า, ยิงปลา และเกมอื่นๆ อีกมากมายผ่านทางเข้าเดียวกัน เว็บได้รับการรับรองจากผู้ใช้งานทั่วโลกและความนิยมเพราะคุณภาพการนำเสนอเกมพนันที่ดีที่สุดบน Siam855 ทำให้คุณสามารถค้นหาและเล่นเกมที่คุณต้องการได้อย่างง่ายดาย
เว็บเดิมพัน Siam855 ยังคงเป็นเว็บไซต์พนันบอลออนไลน์ที่ถูกยกย่องว่าเป็นคุ้มค่าที่สุดในประเทศไทย ปี 2025 เว็บไซต์การแทงบอลของ Siam855 กลายเป็นที่นิยมอย่างมากในวงการเดิมพันในประเทศ นับถือและได้รับการอนุมัติตามกฎหมายจากองค์กรด้านความปลอดภัย เป็นเว็บพนันที่เต็มเปี่ยมไปด้วยความเชื่อถือและความมั่นคง ภายในเว็บไซต์นี้ คุณจะพบกับรูปแบบการแสดงผลการเดิมพันที่น่าสนใจและโปรโมชั่นที่น่าตื่นเต้นมากมาย ไม่ว่าคุณจะเป็นนักเล่นใหม่หรือเคยเล่นมาก่อน ทุกคนจะพบความสนใจในเว็บไซต์นี้ได้แน่นอน
👍 ข้อดีของ Siam855 เว็บแทงบอล:
- เริ่มต้นเดิมพันที่ย่อมเป็นส่วนน้อย: การเริ่มต้นเดิมพันที่เพียงแค่ 10 บาทให้โอกาสให้ผู้เล่นที่มีความรู้สึกไม่แน่ใจหรือเริ่มใหม่ที่จะลองด้วยเงินน้อย นี่เป็นข้อเสนอที่เหมาะสำหรับคนที่ต้องการสัมผัสประสบการณ์การเดิมพันแบบน้อยค่าแต่ก็มีโอกาสสร้างกำไรมากกว่าที่คาดคิดเมื่อถูกในเกมบอล
- กำไรสูงกว่า 100 เท่าของเงินเดิมพัน: โอกาสในการทำกำไรกว่า 100 เท่าจากยอดเงินเดิมพันที่เริ่มต้นเพียง 10 บาทเป็นโอกาสที่น่าตื่นเต้นอย่างแน่นอน ถ้าคุณมีความรับผิดชอบในการเดิมพันและทราบการวิเคราะห์ สิ่งนี้อาจเป็นโอกาสที่ดีในการสร้างรายได้จากเกมบอล
👎 ข้อเสียของ Siam855 เว็บแทงบอล:
- ความเสี่ยงสูงเมื่อเทียบกับเงินที่เดิมพัน: การมีโอกาสทำกำไรมากกว่า 100 เท่านั้นมาพร้อมกับความเสี่ยงที่สูงขึ้น ถ้าคุณไม่มีความรับผิดชอบในการเดิมพันหรือไม่มีการวิเคราะห์ที่ถูกต้อง คุณอาจสูญเสียเงินเดิมพันของคุณได้
IB8 เว็บพนันบอล ไม่ผ่านเอเย่นต์ มาตรฐานสากล 100%
เว็บพนันบอล IB8 ไม่ผ่านเอเย่นต์ เป็นมาตรฐานสากล 100% ที่มอบประสบการณ์การเดิมพันที่เหนือชั้น ด้วยความเชื่อมั่นในความปลอดภัยและความน่าเชื่อถือ IB8 เป็นเว็บพนันออนไลน์ที่สร้างสรรค์ขึ้นเพื่อมอบการพนันที่ครอบคลุมครบวงจรทั้งเกมส์พนันกีฬาและคาสิโน โดยนักเดิมพันสามารถเพลิดเพลินกับเกมยิงปลา กีฬาต่างๆ และเกมคาสิโนหลากหลาย ไม่ว่าจะเป็นบนคอมพิวเตอร์หรือมือถือ รองรับทั้ง iOS และ Android
นอกจากโปรโมชั่นโบนัสไม่อั้นแล้ว ยังมีการอัพเดตเกมเดิมพันให้ใหม่และน่าสนใจตลอดเวลา เพื่อให้นักเดิมพันสามารถสนุกและมีโอกาสทำกำไรได้อย่างต่อเนื่อง แม้ว่าจำนวนผู้เข้าเดิมพันหน้าเว็บจะมีมากกว่า 50,000 คนต่อวัน แต่เว็บพนัน IB8 ยังคงรักษามาตรฐานความปลอดภัยอย่างเข้มงวด เพื่อให้ผู้เล่นมั่นใจในการที่จะเดิมพันและรับรองว่าคุณสามารถเดิมพันได้เงินจริงแน่นอน 100% ด้วยความน่าเชื่อถือที่ได้รับจากผู้ใช้งานจริง ทั้งในประเทศไทยและต่างประเทศ IB8 เป็นทางเลือกที่มั่นคงสำหรับผู้ที่ต้องการทดลองเดิมพันแทงบอลออนไลน์
👍 ข้อดีของ IB8 เว็บพนันบอล ไม่ผ่านเอเย่นต์:
- ไม่ผ่านเอเย่นต์: IB8 เป็นเว็บพนันที่ไม่ผ่านเอเย่นต์ ทำให้นักเดิมพันสามารถทำการเดิมพันโดยตรงกับเว็บไซต์ โดยไม่ต้องผ่านพนักงานเชิญเดิมพัน ทำให้เพิ่มความสะดวกสบายและเพิ่มความเชื่อถือในการเดิมพันของคุณเอง
- มาตรฐานสากล 100%: IB8 มีมาตรฐานความปลอดภัยและความน่าเชื่อถือที่สูงสุด การเดิมพันและการทำธุรกรรมการเงินของคุณจะได้รับการปกป้องอย่างเข้มงวด แน่นอนว่าความน่าเชื่อถือของการทำธุรกรรมกับเว็บนี้จะไม่น่าเป็นห่วง
- ความหลากหลายในการเดิมพัน: IB8 มีการนำเสนอความหลากหลายในการเดิมพัน ทั้งเดิมพันบอล และการเดิมพันอื่นๆ เช่น เกมคาสิโน ทำให้คุณสามารถเลือกเล่นและสนุกไปกับเกมที่คุณชื่นชอบ
👎 ข้อเสียของ IB8 เว็บพนันบอล ไม่ผ่านเอเย่นต์:
- ประสิทธิภาพเว็บไซต์ไม่เสถียรบางครั้ง: บางครั้งอาจมีปัญหาเล็กน้อยเกี่ยวกับประสิทธิภาพของเว็บไซต์ เช่น การโหลดหน้าเว็บที่ช้าหรือปัญหาการเชื่อมต่อที่ไม่เสถียร ซึ่งอาจส่งผลให้ประสบการณ์การเดิมพันของคุณเป็นอย่างย่ำลงบ้าง
Lucky Block – เว็บพนันบอลออนไลน์อันดับหนึ่งที่มองเครดิตสูงสุดถึง 10,000 บาท
Lucky Block ให้บริการเว็บแทงบอลออนไลน์ด้วยอัตราต่อรองที่เป็นธรรมที่ถูกคำนวณมาแล้วไม่ทำให้ผู้เล่นเสียเปรียบ โดยทาง Lucky Block ได้ทำการเปิดรับแทงด้วยตนเอง
และไม่ได้ให้บริการเฉพาะการแทงบอลเท่านั้น ยังมีกีฬาอื่น ๆ ที่ให้บริการด้วย เช่น บาสเกตบอล อเมริกันฟุตบอล ปิงปอง เทนนิส และอื่น ๆ อีกมากมาย
สำหรับลูกค้าที่ทำการสมัครสมาชิกครั้งแรกจะได้รับโอกาสรับโบนัสต้อนรับ 200% สูงสุด 10,000 ยูโร + 50 ฟรีสปิน เพียงฝากขั้นต่ำ 40 ยูโรเท่านั้น
ไม่จำเป็นต้องใช้สกุลเงินดิจิทัลเพียงอย่างเดียวในการฝาก หากไม่มีสินทรัพย์สามารถแลกเปลี่ยนได้โดยอิงอัตราแลกเปลี่ยนตามธนาคารโลก และหากมีข้อสงสัยใด ๆ สามารถติดต่อแอดมินผ่านไลฟ์แชทหน้าเว็บได้ตลอด 24 ชั่วโมงไม่มีวันหยุด
👍 ข้อดี:
- รองรับการชำระด้วยสกุลเหรียญคริปโต 14 สกุล
- บริการไลฟ์แชทตลอด 24/7 ไม่มีวันหยุด
- โบนัสต้อนรับสูงสุด 10,000 ยูโร เพียงฝาก 40 ยูโรขึ้นไป
- รองรับการใช้งานด้วยภาษาไทย
- เกมให้เลือกมากหลายพันเกมด้วยกัน
👎 ข้อเสีย:
- ยังไม่มีบริการแอปพลิเคชั่น
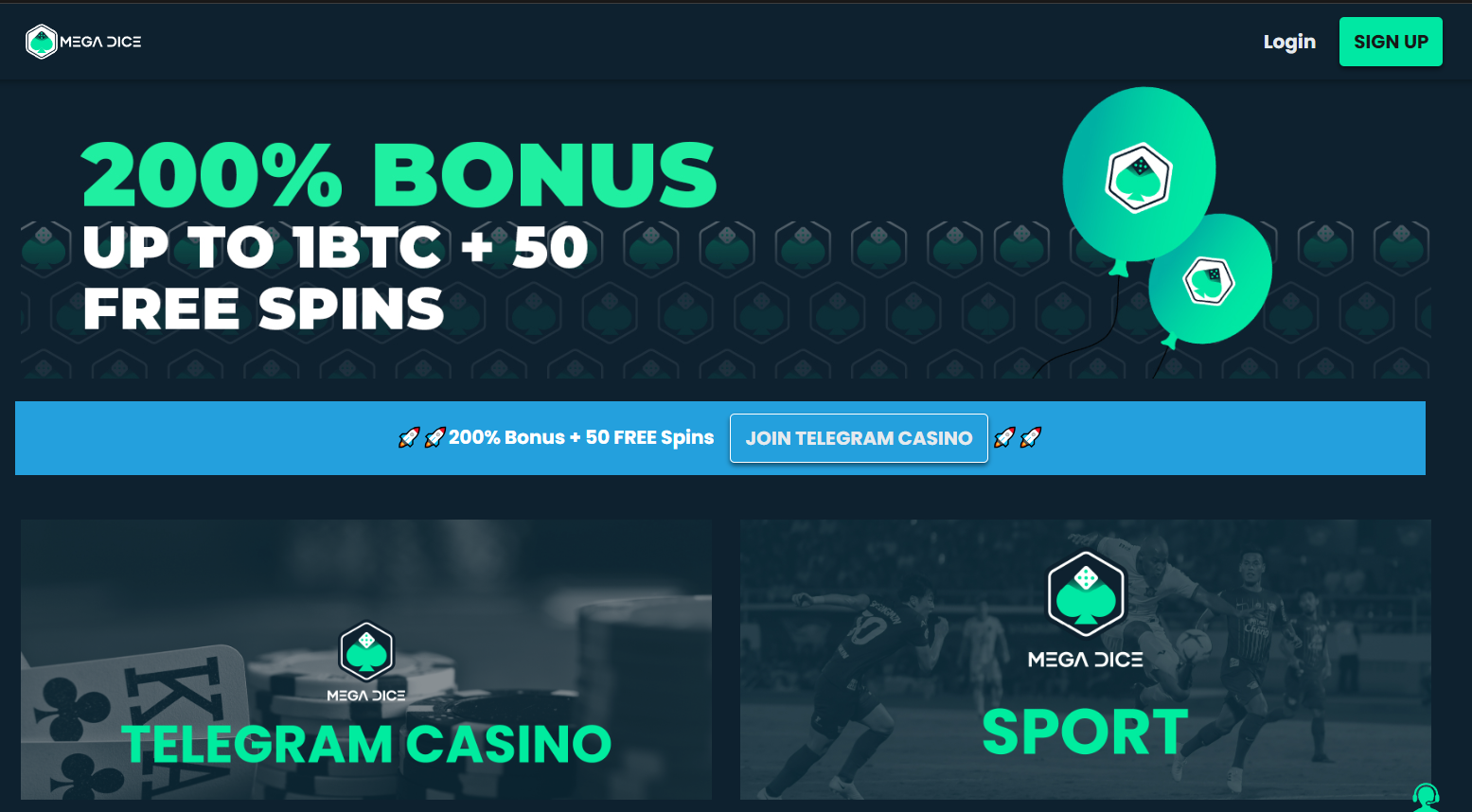
Megadice – ให้บริการเดิมพันเกมกีฬาที่รองรับการชำระด้วยคริปโตหลายสกุล
Megadice เป็นเว็บแทงบอลออนไลน์อีกหนึ่งแห่งที่ให้บริการเกมคาสิโน สล็อต คาสิโนสด เกมโชว์ เกมกีฬา จากค่ายเกมชั้นนำอย่าง Hacksaw Gaming, Pragmatic Play, Evolution, Spribe, Octoplay, AvatarUX, NetEnt, Relax Gaming, Red Tiger และอื่น ๆ
นอกเหนือจากเกมกีฬาที่อัตราเดิมพันที่ค่อนข้างเอื้อประโยชน์ต่อผู้พนันแล้ว ยังมีบริการไลฟ์แชทตลอด 24 ชั่วโมงสำหรับผู้ที่ต้องการสอบถามเกี่ยวกับโปรโมชั่นเพิ่มเติมหรือแจ้งปัญหาการใช้งาน
คุณไม่จำเป็นต้องมีสินทรัพย์ดิจิทัลในการฝาก เพียงแค่แลกเปลี่ยนบิทคอยน์ในเว็บไซต์ก็สามารถทำการเทรดเบื้องต้นได้ อีกทั้งอัตราการแลกเปลี่ยนยังเป็นไปตามเฟดหรือธนาคารโลก
และหากผู้ใช้งานมีสกุลเงินดิจิทัลครอบครอง ก็สามารถนำมาทำการฝากได้ โดยจะได้โบนัสฝากครั้งแรก 200% สูงสุด 1BTC + 50 ฟรีสปินในเกม Wanted Dead or a Wild
👍 ข้อดี:
- บริการเกมคาสิโนหลากหลายประเภท จากค่ายชั้นนำ
- สนับสนุนลูกค้าผ่านทางไลฟ์แชท
- มีระบบรอยัลลิตี้ด้วยการสะสมคะแนนแลกรางวัลพิเศษ
- กิจกรรมทัวร์นาเมนต์ที่น่าสนใจ
- โบนัสสูงสุดถึง 1BTC หรือ บิทคอยน์ 1 เหรียญ
👎 ข้อเสีย:
- สำหรับสกุลเงินทั่วไปใช้ยูโรเป็นหลัก
Me88 เว็บทางเข้า แทงบอล เว็บตรง ไม่ผ่านเอเย่นต์ เงินจริง 100%
เว็บพนันบอล Me88 ประตูสู่ความบันเทิงแห่งการแทงบอล เว็บตรง ไม่ต้องผ่านเอเย่นต์! ที่นี่คุณจะพบกับโอกาสทองในการเดิมพันกับเงินจริง 100% และแน่นอนทุกการเดิมพันเป็นที่สนุกไปกับเว็บไซต์ที่ห้ามพลาด Fun88 ซึ่งมีชื่อเสียงระดับโลกในการพนันออนไลน์ เต็มไปด้วยประสบการณ์ที่ยาวนานในการให้บริการแทงบอลออนไลน์ทั้งในเมืองไทยและเทศอื่น ๆ ไม่ว่าจะเป็นประเทศจีนหรือฟิลิปปินส์ ทั้งยังได้รับใบอนุญาตจากหน่วยงานหลายแห่ง เช่น Isle of Man Gambling Supervision Commission และ First Cagayan Leisure & Resort Corporation และอีกมากมาย
ในระยะเวลากว่า 5 ปี Me88 ไม่เพียงแค่ให้บริการการแทงบอลออนไลน์ แต่ยังมีสิ่งมหัศจรรย์อื่น ๆ รอคุณอยู่ เช่น การเดิมพันบาสเก็ตบอล วอลเล่ห์บอล และการเล่นพนันแบบหลากหลายอื่น ๆ นอกจากนี้ คุณยังสามารถเพิ่มความมันส์ด้วยโปรโมชั่นต่าง ๆ ที่ Me88 มีเสมอ ไม่ว่าจะเป็นโบนัสเงินฝากขั้นต่ำ สิทธิพิเศษในการรับเสื้อฟุตบอลพรีเมียร์ลีก และโอกาสหมุนสล็อตฟรีถึง 15 ครั้ง เพื่อให้คุณได้มีประสบการณ์การเล่นที่ยิ่งใหญ่และน่าจดจำ!
👍 ข้อดีของ Me88 เว็บทางเข้า แทงบอล:
- เว็บตรงและไม่ผ่านเอเย่นต์: Me88 เป็นเว็บที่ให้บริการแทงบอลและเกมคาสิโนโดยตรง ไม่ผ่านเอเย่นต์หรือตัวแทนกลาง ซึ่งทำให้ผู้ใช้ได้รับประสบการณ์การเดิมพันที่โปร่งใสและมั่นใจในความปลอดภัยของข้อมูลส่วนตัวและการทำธุรกรรมทางการเงินของตนเองมากขึ้น
- เงินจริง 100%: เว็บไซต์รับรองว่ามีการจ่ายเงินรางวัลจริง 100% ตามผลการเดิมพันที่ผู้ใช้ทำไว้ นั่นหมายความว่าผู้เล่นสามารถมั่นใจได้ว่าจะได้รับเงินรางวัลตามที่คาดหวัง
- ความหลากหลายในเกม: Me88 นอกจากการแทงบอลแล้วยังมีเกมคาสิโนออนไลน์หลากหลายเกมให้เลือกเล่น เช่น สล็อตออนไลน์ รูเล็ต บาคาร่า และเกมส์คาสิโนอื่นๆ ที่สามารถทดลองเล่นหรือเล่นเงินจริงได้
👎 ข้อเสียของ Me88 เว็บทางเข้า แทงบอล:
- ข้อจำกัดในการเดิมพัน: อาจมีการจำกัดในรูปแบบการเดิมพันบางประเภทหรือการเดิมพันในเหตุการณ์บางรายการ ซึ่งอาจทำให้ผู้ใช้ไม่สามารถเข้าถึงตลอดเวลาที่ต้องการ
EUBET เว็บพนันบอล ถูกกฎหมาย แจกโบนัส สูงสุด 1,000%
EUBET เว็บพนันบอลที่ถูกกฎหมายและมอบโอกาสให้แทงบอลออนไลน์อย่างน่าสนใจ ด้วยโปรโมชั่นโบนัสที่สูงสุดถึง 1,000% นี่คือเว็บไซต์เดิมพันออนไลน์ที่นับวันเปิดให้บริการมานานกว่า 3-5 ปี ด้วยความเชี่ยวชาญในวงการการเดิมพันออนไลน์ ทำให้ EUBET เป็นที่ยอมรับอย่างแข็งแกร่ง เว็บไซต์นี้มีความหลากหลายในเกมส์เดิมพันกีฬาออนไลน์มากมายให้เลือกเล่น พร้อมกับการนำเสนอโปรโมชั่นและโบนัสออนไลน์สำหรับผู้ใช้บริการเป็นประจำ ด้วยการออกแบบระบบเล่นที่ใช้งานง่าย
การเดิมพันบนเว็บ EUBET ไม่จำเป็นต้องใช้เวลามาก แม้คุณจะไม่เคยลองเดิมพันก่อนก็ตาม เนื่องจากเว็บไซต์นี้ได้ถูกออกแบบมาเพื่อให้เหมาะสมและง่ายต่อการใช้งานสำหรับผู้เล่นทุกระดับ นอกจากนี้ การเดิมพันออนไลน์กับ EUBET ยังเป็นไปได้อย่างสะดวกสบาย โดยคุณสามารถเข้าถึงและแทงบอลได้ทั้งบนคอมพิวเตอร์และแอฟพพลิเคชั่น ที่ทำให้การเดิมพันของคุณเป็นเรื่องง่ายและสะดวกสบายมากยิ่งขึ้น เพิ่มความสนุกและความตื่นเต้นในการเดิมพันอย่างมาก
👍 ข้อดีของ EUBET เว็บพนันบอล ถูกกฎหมาย:
- ถูกกฎหมายและน่าเชื่อถือ: EUBET เป็นเว็บพนันบอลที่ได้รับการอนุญาตและกำหนดตามกฎหมาย ทำให้ผู้เล่นสามารถเชื่อมั่นในความปลอดภัยและความน่าเชื่อถือของเว็บไซต์ในการทำการเดิมพัน
- โบนัสสูงสุด 1,000%: EUBET มอบโอกาสให้ผู้เล่นได้รับโบนัสสูงสุดถึง 1,000% ทำให้มีโอกาสทดลองเดิมพันและเพิ่มโอกาสในการทำกำไรอย่างมาก
- ความหลากหลายในการเดิมพัน: เว็บไซต์นี้มีการนำเสนอทั้งเกมพนันบอลและเกมอื่นๆ ที่คุณสามารถเดิมพันและเล่นได้ ทำให้มีความหลากหลายในการเลือกเดิมพันและสนุกสนานมากยิ่งขึ้น
👎 ข้อเสียของ EUBET เว็บพนันบอล ถูกกฎหมาย:
- ข้อจำกัดในการใช้โบนัส: อาจมีข้อจำกัดในการใช้โบนัสที่สามารถใช้งานได้กับบางเกมหรือในบางสถานการณ์ ทำให้ผู้เล่นต้องอ่านและเข้าใจเงื่อนไขของโบนัสก่อนที่จะเริ่มทำการเดิมพันเพื่อป้องกันความสับสนและความผิดหวังในภายหลัง
77Bet เดิมพัน พนันบอล ได้เงินจริง ราคาดีที่สุดในไทย ปี 2025
77Bet เดิมพันบอล ได้เงินจริง ราคาดีที่สุดในไทย ปี 2025 คือเว็บไซต์พนันออนไลน์ที่ก่อตั้งขึ้นในปี 2015 และได้รับความเคารพมาอย่างยาวนานมากกว่า 8 ปี เว็บไซต์นี้ยังได้รับใบอนุญาตจาก Philippine Amusement & Gaming Corporation (PAGCOR) ในประเทศฟิลิปปินส์ ทำให้ผู้ใช้มั่นใจในความเชื่อถือ เพื่อความปลอดภัยของผู้ใช้ 77Bet ใช้ระบบ SSL เพื่อป้องกันการเข้าถึงข้อมูลจากบุคคลที่ไม่ได้รับอนุญาต นักเดิมพันสามารถเดิมพันได้อย่างแน่นอน และทำเงินจากการเดิมพันกีฬาออนไลน์ได้อย่างแท้จริง
เว็บไซต์ 77Bet นับได้ถึง 6 เกมส์เดิมพันที่ผู้เล่นสามารถเลือกเล่น และยังมีการแข่งขันแบบทัวร์นาเมนต์ให้ผู้เล่นมีโอกาสชิงโบนัสในทุกเดือน การเข้าสู่ระบบ 77Bet ง่ายดายเพียงเข้าไปที่เว็บแทงบอล เหมือนกับการเล่นในเว็บไซต์ 77Bet เนื่องจากเป็นตัวแทนโดยตรงจากเว็บไซต์แทงบอล นอกจากนี้ 77Bet ยังมีโปรโมชั่นฟรีเครดิตที่จัดให้ไม่ยั้งเพราะสามารถเพิ่มความสนุกให้กับผู้เล่นได้อย่างมาก วิธีการทำฝากเงินที่ 77Bet ไม่ซับซ้อนเช่นกัน เพียงเลือกวิธีเติมเงินที่คุณต้องการ และทำการเติมเงินเข้าสู่ 77Bet ได้อย่างง่ายดาย
👍 ข้อดีของ 77Bet พนันบอล ได้เงินจริง:
- ราคาดีที่สุดในไทย: 77Bet มุ่งเน้นการนำเสนอราคาการต่อรองที่ดีที่สุดในไทย ทำให้ผู้เล่นสามารถแทงบอลด้วยราคาที่เหมาะสมและมีโอกาสทำกำไรสูง
- เดิมพันได้เงินจริง: 77Bet เป็นเว็บไซต์ที่ผู้เล่นสามารถทดลองและแทงเดิมพันในรูปแบบต่างๆ โดยมีโอกาสที่จะได้รับเงินจริงเมื่อทำการเดิมพันกับทีมอีสปอร์ตที่ชื่นชอบ
- ความปลอดภัยและน่าเชื่อถือ: 77Bet ได้รับใบอนุญาตจาก Philippine Amusement & Gaming Corporation (PAGCOR) ที่เป็นองค์กรรับรองในการให้บริการพนันออนไลน์ ทำให้ผู้เล่นมั่นใจในความน่าเชื่อถือและความปลอดภัยของเว็บไซต์
👎 ข้อเสียของ 77Bet พนันบอล ได้เงินจริง:
- อาจมีความยุ่งยากในการเข้าถึงบางครั้ง: บางครั้งผู้เล่นอาจพบปัญหาในการเข้าถึงเว็บไซต์ หรือมีความยุ่งยากในการทำรายการบางอย่าง อย่างไรก็ตาม นี่เป็นปัญหาที่เกิดขึ้นไม่บ่อยๆ และไม่ได้ส่งผลกระทบมากนักในการเล่นแทงบอล
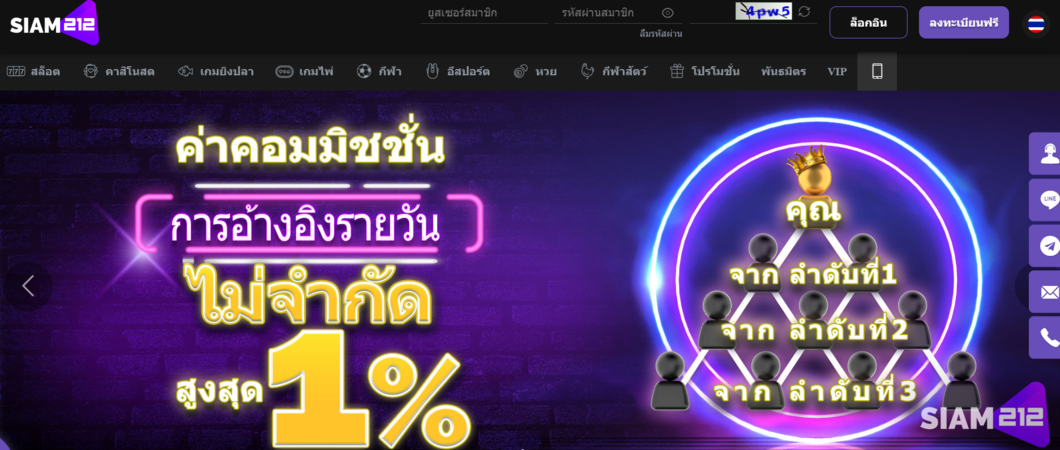
Siam212 เว็บแทงบอลออนไลน์ ขั้นต่ำ 10 บาท ค่าน้ำดีที่สุด แทงบอลได้ทุกคู่
Siam212 เว็บแทงบอลออนไลน์ที่มีขั้นต่ำเพียง 10 บาท และค่าน้ำที่ดีที่สุดในวงการ ท่านสามารถแทงบอลทุกคู่การแข่งขันได้อย่างอิสระบนเว็บไซต์เดิมพันแทงบอลออนไลน์ Siam212 ซึ่งเปิดให้บริการมาเกือบ 5 ปี และเป็นที่ยอมรับเป็นอย่างดีในการดำเนินงานอย่างมั่นคงและปลอดภัยต่อนักแทงบอลออนไลน์ หลากหลายโอกาสในการเดิมพันจากหลากหลายมุมมองรออยู่ให้คุณเลือก
รวมถึงการเดิมพันบนเว็บไซต์ Siam212 ซึ่งเป็นเว็บเดิมพันออนไลน์ระดับมาตรฐานสากล และได้รับการยอมรับในประเทศฟิลิปปินส์ ทั้งนี้คุณสามารถที่จะแทงบอลได้ทั้งบนเว็บคอมพิวเตอร์และมือถือ ในทุกที่ทุกเวลาที่คุณต้องการ แค่คุณเชื่อมต่อกับอินเตอร์เน็ต คุณก็สามารถเข้าสู่แอพพลิเคชั่นแทงบอล Siam212 และทำการเดิมพันได้ตามสบาย
เว็บไซต์ Siam212 นี้ ยังมีรายละเอียดการเดิมพันหลากหลาย ไม่ว่าจะเป็นการเดิมพันบอลเดี่ยว แทงบอลชุด บอลเสต็ป และรูปแบบการแทงอื่นๆ ที่สามารถเลือกเล่นตามความชอบของคุณได้ สำหรับผู้ที่สนใจเข้าร่วมสนุกและเพลิดเพลินกับการเดิมพัน คุณสามารถสมัครสมาชิกเพื่อรับโปรโมชั่นที่อัพเดตอยู่เป็นระยะๆ โดยเฉพาะสำหรับนักแทงบอลออนไลน์ คุณจะได้รับโปรโมชั่นที่จัดเตรียมไว้ให้คุณอย่างต่อเนื่อง อีกทั้งยังมีโปรโมชั่นเพื่อนำเสนอให้แก่แฟนบอลอีกด้วย ที่สนุกและน่าตื่นเต้น
👍 ข้อดีของ Siam212 เว็บแทงบอลออนไลน์ ขั้นต่ำ 10 บาท:
- ขั้นต่ำเพียง 10 บาท: Siam212 มีขั้นต่ำในการเดิมพันเพียง 10 บาทเท่านั้น นั้นหมายความว่าผู้เล่นสามารถเข้าร่วมการเดิมพันและลุ้นรางวัลได้ด้วยเงินที่น้อยที่สุด ทำให้มีความสะดวกและเหมาะสมสำหรับผู้ที่ต้องการลองเล่นหรือแทงบอลครั้งแรกๆ
- ค่าน้ำดีที่สุด: เว็บไซต์ Siam212 มีค่าน้ำที่ดีที่สุดในวงการ นั่นหมายความว่าผู้เล่นจะได้รับการตัดสินใจที่สุดที่เหมาะสมในการเลือกแทงและเข้าร่วมการเดิมพัน ทำให้มีโอกาสที่ดีกว่าในการสร้างกำไร
- สะดวกสบายและใช้งานง่าย: Siam212 นับถือความสะดวกสบายและความง่ายในการใช้งาน เว็บไซต์มีอินเตอร์เฟซที่ใช้งานง่าย รวมถึงรองรับการใช้งานทั้งบนคอมพิวเตอร์และอุปกรณ์มือถือ เพียงเชื่อมต่ออินเตอร์เน็ตคุณก็สามารถเข้าถึงและแทงบอลได้ทุกที่ทุกเวลา
👎 ข้อเสียของ Siam212 เว็บแทงบอลออนไลน์ ขั้นต่ำ 10 บาท:
- มีข้อจำกัดการถอนเงิน: นักเดิมพันจำเป็นต้องถอนเงินขั้นต่ำ 500 บาท เพื่อหลีกเลี่ยงค่าธรรมเนียมการถอน แต่ทั้งนี้แล้วก็สามารถโอนเงินเข้าธนาคารได้ทั่วไทย เพียงไม่กี่นาทีเท่านั้น
22Fun แทงบอลเต็ง ครบวงจร เปิดตลอด 24 ชั่วโมง
22Fun เว็บไซต์แทงบอลเต็งที่ครบวงจรและเปิดให้บริการตลอด 24 ชั่วโมง เป็นแบรนด์ที่มีชื่อเสียงทางการพนันออนไลน์ ที่มุ่งเน้นการเดิมพันในทีมอีสปอร์ตที่มีชื่อเสียงเช่น PLM และยังมีเกมส์กีฬาอื่นๆ ให้เลือกเล่นอีกหลากหลาย เว็บไซต์นี้นำเสนออัตราการต่อรองที่สมดุลและโปรโมชั่นที่หลากหลายให้ผู้เล่นเลือกใช้ตามความต้องการ ได้รับการรับรองความปลอดภัยจาก BMM และ GLI เพื่อให้ความมั่นใจในการทำการเดิมพัน
เว็บแทงบอลออนไลน์นี้ ยังเป็นพาร์ทเนอร์กับทีมอีสปอร์ต PLM อันดับหนึ่งของประเทศไทย และคุณสามารถเลือกเดิมพันได้ทั้งบนคอมพิวเตอร์และมือถือ แม้กระทั่งการเล่นบนมือถือยังอาจไม่เสถียรเท่าที่ควร สำหรับความปลอดภัย 22Fun ได้รับการรับรองจาก Philiphin Ceza&Pagcor และมีอัตราการต่อรองที่สมดุล และความเสถียรในการเล่นที่มีคุณภาพ บนเว็บไซต์นี้ได้รับการรับรองอย่างชัดเจน จึงเป็นทางเลือกที่ดีกว่าการก็อปปี้อัตราการต่อรองจากเว็บไซต์อื่น
👍 ข้อดีของ 22Fun แทงบอลเต็ง ครบวงจร:
- ความครบวงจร: เว็บไซต์ 22Fun มุ่งให้บริการครบวงจรที่ครอบคลุมทุกด้านของการแทงบอลเต็ง ไม่ว่าจะเป็นการเดิมพันในทีมอีสปอร์ตที่ได้ชื่อว่าดังเช่น PLM หรือเกมส์กีฬาอื่นๆ ที่ท้าให้ผู้เล่นได้สนุกและสามารถแทงกีฬาที่ตนชื่นชอบได้
- การให้บริการตลอด 24 ชั่วโมง: 22Fun เปิดให้บริการตลอด 24 ชั่วโมงทั้งวันทั้งคืน เพื่อให้ผู้เล่นสามารถทดลองเล่นหรือทำการเดิมพันตามสะดวกเวลาที่เหมาะสม
- อัตราการต่อรองที่เหมาะสม: เว็บไซต์นี้นำเสนออัตราการต่อรองที่ไม่สูงมากแต่เป็นราคาที่เหมาะสม ทำให้ผู้เล่นสามารถทำการเดิมพันในเวลาที่มีความน่าสนใจได้อย่างมีความมั่นใจ
👎 ข้อเสียของ 22Fun แทงบอลเต็ง ครบวงจร:
- อาจจะยังไม่มีเกมกีฬามากเท่าไหร่นัก: เว็บเดิมพันนี้มีการนำเสนอ เกมคาสิโน และ เกมแทงบอลออนไลน์ ครบวงจร แต่อาจจะยังไม่มีเกมเดิมพันกีฬามากเท่าที่ควร
iVip9 เว็บพนัน แทงบอล ครบวงจร เรียลไทม์ เงินจริง ที่ดีที่สุดในไทย
iVip9 เว็บพนัน แทงบอล ครบวงจร เรียลไทม์ เงินจริง ที่ดีที่สุดในไทย เว็บไซต์พนันบอลออนไลน์ iVip9 ถือเป็นที่รู้จักอย่างกว้างขวางทั่วโลก และเป็นสถานที่พบการพนันออนไลน์ที่ครบวงจรที่สุด คุณสามารถแทงบอลเป็นเวลาจริงและได้รับเงินจริงผ่านเว็บนี้ได้อย่างง่ายดาย เว็บไซต์นี้ได้รับความนิยมมากที่สุดในประเทศไทย และเป็นที่ไว้วางใจของผู้ใช้งานจำนวนมาก
บริษัทมีใบอนุญาตระดับสากลในหลายประเทศ ส่งเสริมความเชื่อมั่นให้กับนักพนันหลายคนที่เลือกเล่นพนันบอลในเว็บไซต์นี้ เนื่องจาก iVip9 ได้รับการสปอนเซอร์จากทีมบอลชื่อดังอย่าง West Ham United และ Cardiff City นอกจากนี้ คุณยังสามารถเพลิดเพลินกับการเล่นคาสิโนออนไลน์กับ iVip9 ทั้งบนเครื่องคอมพิวเตอร์และมือถือ ด้วยความสะดวกสบายตามที่คุณต้องการ แค่คุณมีการเชื่อมต่ออินเตอร์เน็ตเท่านั้น
👍 ข้อดีของ iVip9 เว็บพนันแทงบอล:
- ความสะดวกสบายการเดิมพันครบวงจร: iVip9 เป็นเว็บพนันที่ให้บริการครบวงจรทั้งการแทงบอลและคาสิโนออนไลน์ ผู้เล่นสามารถเข้ามาเดิมพันทันทีและสลับระหว่างการเดิมพันที่ตนเองต้องการได้ในเว็บเดียวเท่านั้น นั่นทำให้มีความสะดวกสบายและไม่ต้องย้ายเว็บไปมา เพื่อสนุกกับการเล่น
- เล่นเรียลไทม์ รับเงินจริง: การเดิมพันและการเล่นเกมใน iVip9 เป็นเรียลไทม์ ผู้เล่นสามารถเห็นผลลัพธ์และผลตอบแทนที่เกิดขึ้นทันที เมื่อชนะกันได้ คุณจะได้รับเงินจริงตามอัตราการจ่ายเงินที่กำหนดไว้ ทำให้คุณสามารถเพลิดเพลินกับความสนุกและมีโอกาสในการทำกำไรได้อย่างทันที
👎 ข้อเสียของ iVip9 เว็บพนันแทงบอล:
- ขั้นต่ำการฝากและการถอน: เว็บเดิมพัน แทงบอลออนไลน์ iVip9 ยังมีข้อกำหนดขั้นต่ำ การฝากและการถอน อยู่ที่ 300 บาท นี่ก็อาจจะเป็นข้อเสียสำหรับนักเดิมพันมือใหม่ก็ได้เช่นกัน
88sanook เล่นพนันบอล มือถือ แจกโบนัสสมาชิกใหม่ 1,000 บาทฟรี
88sanook เป็นเว็บพนันบอลบนมือถือที่น่าสนใจมาก สำหรับสมาชิกใหม่ที่เข้าร่วม จะได้รับโบนัสเป็นเงิน 1,000 บาทฟรี เว็บไซต์พนันบอล 88sanook ได้เปิดให้บริการมานานกว่า 10 ปีแล้ว และเป็นเว็บที่มีชื่อเสียงในการให้บริการเดิมพันกีฬาออนไลน์ในอันดับต้น ๆ ของประเทศไทย เว็บนี้มีบริการที่น่าสนใจมากมาย เพื่อเพิ่มความมั่นใจให้กับนักพนันทุกท่านอย่างเต็มที่ เราสามารถพูดถึงความคุ้มค่าที่ตามมากับการเข้าร่วมเป็นสมาชิกกับเว็บนี้ได้อย่างมาก ไม่เพียงแต่เฉพาะการเดิมพันฟุตบอลเท่านั้น แต่ยังมีการเสนอเกมพนันออนไลน์ทุกประเภทอีกด้วย ทำให้เว็บ 88sanook เป็นที่พึ่งได้สำหรับผู้ที่ชื่นชอบการเล่นพนันออนไลน์ทั้งหมด
ระบบฝากเงินถือเป็นระบบที่ทันสมัยและสามารถรองรับการใช้งานได้อย่างเต็มที่ โดยท่านสามารถทำรายการในการฝากเงินได้ในเวลาไม่เกิน 1 นาที ในขณะเดียวกัน ระบบถอนเงินยังมีขั้นตอนที่ง่ายกว่า และท่านสามารถทำรายการในการถอนเงินได้อย่างรวดเร็วโดยใช้เวลาไม่เกิน 1 นาที เว็บไซต์นี้มีบริการเดิมพันทางกีฬาให้ท่านเลือกมากมาย เช่น ฟุตบอล, บาสเกตบอล และกีฬาอื่น ๆ อีกมากมาย รองรับทั้ง Android และ IOS รวมถึงคอมพิวเตอร์ด้วย เพื่อให้ท่านสามารถเข้าถึงและเล่นเกมพนันได้อย่างสะดวกสบายตามที่คุณต้องการ
👍 ข้อดีของ 88sanook เว็บพนันบอล:
- โบนัสสมาชิกใหม่: เว็บไซต์ 88sanook ท่านจะได้รับโบนัสเงินสด 1,000 บาทเมื่อสมัครเป็นสมาชิกใหม่ ซึ่งเป็นโอกาสที่ดีในการเริ่มเดิมพันและทดลองเล่นได้โดยไม่ต้องใช้เงินของท่านเอง นี่เป็นข้อเสนอที่น่าสนใจสำหรับผู้ที่สนใจลองเล่นและทดสอบเว็บเดิมพัน
- ความสะดวกสบายในการเล่นผ่านมือถือ: ด้วยการเล่นพนันบอลผ่านมือถือที่เว็บ 88sanook ท่านสามารถเข้าร่วมเดิมพันและเล่นเกมได้ทุกที่ทุกเวลา ไม่จำเป็นต้องพกพาคอมพิวเตอร์ นี่เป็นทางเลือกที่สะดวกสบายสำหรับผู้ที่ต้องการทำรายการเดิมพันขณะเดินทางหรืออยู่นอกบ้าน
👎 ข้อเสียของ 88sanook เว็บพนันบอล:
- ข้อจำกัดของโบนัส: การรับโบนัสสมาชิกใหม่มากับเงื่อนไขและข้อกำหนดบางอย่าง ท่านอาจต้องทำการวางเงินเดิมพันตามเงื่อนไขก่อนที่จะสามารถถอนเงินได้ ดังนั้นควรอ่านและทำความเข้าใจเงื่อนไขในการใช้โบนัสก่อนที่จะเริ่มเล่น
โหมดแทงบอลออนไลน์ มีรูปแบบไหนบ้าง ?
เว็บแทงบอลออนไลน์นำเสนอเกมในหลากหลายรูปแบบ ท่านสามารถเลือกเดิมพันในเว็บพนันบอลออนไลน์ได้ตามความชอบของท่าน และมีรูปแบบการเดิมพันที่หลากหลายเพื่อให้ท่านสามารถเพลิดเพลินกับการเล่นได้ ไม่ว่าจะเป็น การแทงบอลแบบคู่เดียว, แทงบอลชุด, แทงบอลสด (LIVE), แทงสเต็ป (Live), แทงบอลเตะมุม และแทงบอลราคาพูล ทั้งหมดนี้เป็นตัวเลือกที่ท่านสามารถเลือกเดิมพันได้ตลอด 24 ชั่วโมง เพื่อให้ท่านสามารถเพลิดเพลินและทดสอบความรู้สึกในการเล่นพนันบอลออนไลน์
เดิมพันกีฬา a-Sport
โหมดเดิมพันกีฬา a-Sport ถือเป็นโหมดที่ได้รับความนิยมสูงสุดในการวางเดิมพันในกีฬาออนไลน์ เนื่องจากมีฟีเจอร์ที่เหมาะสมและง่ายต่อการใช้งาน เป็นพิเศษสำหรับผู้ที่ชื่นชอบการเดิมพันบอลสเต็ป นอกจากนี้ยังมีการให้โบนัสและโปรโมชั่นหลากหลาย รวมถึงมีทางเข้าสู่เว็บเดิมพันบอล ผ่านมือถือให้เลือกใช้มากมาย เพื่อเพิ่มความสนุกสนานในการเดิมพันอย่างต่อเนื่อง ทำให้ท่านสามารถพบกับความสนุกและความตื่นเต้นได้ตลอดเวลา
เดิมพันเกมกีฬา x-Sport
โหมดการเดิมพันเกมกีฬา x-Sport ถูกออกแบบมาเพื่อตอบสนองความต้องการของนักเดิมพันที่ชื่นชอบความตื่นเต้นและไม่ชอบการวางเดิมพันล่วงหน้า ในโหมดนี้ผู้เล่นสามารถที่จะชมกีฬาในรูปแบบสดและวางเดิมพันพร้อมกัน เพื่อสร้างความตื่นเต้นและเร้าใจ ที่สามารถลุ้นรางวัลได้ทันทีในทุก ๆ นาที
เดิมพันเกมกีฬาอีสปอร์ต
การแทงบอล กีฬาอีสปอร์ต ที่เว็บพนันบอลกำลังได้รับความนิยมอย่างกว้างขวาง มีแนวโน้มที่จะได้รับความนิยมมากขึ้นเรื่อย ๆ ในอนาคต บริษัทเว็บแทงบอลออนไลน์ ระบบมือถือ ได้สังเกตถึงความต้องการเหล่านี้และนำเสนอการวางเดิมพัน แทงบอลออนไลน์ ในกีฬาอีสปอร์ต ผู้เล่นสามารถเข้าร่วมการเดิมพันผ่านเว็บไซต์บนมือถือได้เช่นเดียวกัน
วิธีการสมัครสมาชิก พนันบอลออนไลน์
การสมัครสมาชิก เว็บพนันบอลออนไลน์ สามารถทำได้อย่างง่ายดาย ท่านสามารถเข้าสู่เว็บไซต์พนันบอลออนไลน์ผ่านทางเข้าเว็บเพื่อเริ่มกระบวนการสมัครสมาชิก นอกจากนี้ เว็บพนันบอลออนไลน์นี้ยังถูกจัดอันดับว่าเป็นเว็บแทงบอลออนไลน์ที่มีคุณภาพและเป็นที่น่าเชื่อถือ ด้วยระบบเกมเดิมพันที่มีประสิทธิภาพและรวมถึงตัวเลือกเกมเดิมพันบอลออนไลน์ที่หลากหลาย
นักเดิมพันที่สนใจเข้าร่วมเว็บพนันบอล สามารถทำการสมัครสมาชิกได้อย่างง่ายดาย ผ่านทางมือถือหรือโทรศัพท์เพียงไม่กี่ขั้นตอนเท่านั้น และท่านยังสามารถรับโบนัสและโปรโมชั่นเดิมพันผ่านระบบมือถือได้อีกมากมาย เพื่อให้ท่านสามารถเข้าสนุกและเล่นได้อย่างเต็มที่ ทางเราจะมาแนะนำขั้นตอนง่ายๆ ในการสมัครสมาชิก
ทำความรู้จักเว็บพนันบอล ไม่ผ่านเอเย่นต์
เว็บตรง พนันบอลออนไลน์ ฟรีเครดิต ไม่ผ่านเอเย่นต์ นำเสนอเกมเดิมพันการพนันฟุตบอล ครบวงจรมาพร้อมกับตัวเลือกรูปแบบหลากหลายที่ผู้เล่นสามารถเลือกเล่น ทำกำไรมูลค่าได้สูงสุดกว่า 1 ล้านบาท เช่น แทงบอลเต็ง, แทงบอลเสต็ป, แทงบอลสูงต่ำ, แทงบอล 1×2, แทงบอลแฮนดิแคป และอื่นๆ อีกมากมาย
แน่นอนว่าผู้เล่นสามารถเลือกวางเงินเดิมพัน บ้านผลบอล ได้ทุกลีกบอลทั้งในประเทศไทยและต่างประเทศ ลุ้นรับกำไรสูงสุดกว่า 3,000 เท่าของเงินเดิมพัน สามารถเลือกเดิมพันได้ทั้ง แทงบอลออนไลน์ และ แทงบอลสด ที่นักเดิมพันสามารถเลือกเล่นได้แบบเรียลไทม์ สร้างความสนุกสนานกันได้เต็มที่ เหมาะสำหรับนักเดิมพันที่ชื่นชอบการดูบอลออนไลน์
- แทงบอลเต็ง หรือ แทงบอลเดี่ยว เป็นรูปแบบการเดิมพันเพียงแค่ 1 คู่เท่านั้น ลุ้นรับกำไรสูงสุดได้มากกว่า 1,000 เท่าของเงินเดิมพัน เรียกได้ว่าเป็นรูปแบบเกมเดิมพันสุดคุ้มแน่นอน
- แทงบอลเสต็ป หรือ แทงบอลชุด เป็นการเลือกเดิมพันบอล เริ่มต้น 2 คู่ และสูงสุดกว่า 12 คู่ ผู้เล่นสามารถลุ้นรับการทำกำไรได้สูงสุดกว่า 12 คู่ สามารถเดิมพันเกมบอลได้หลากหลายคู่ เหมาะสำหรับนักเดิมพันที่มีงบประมาณการเดิมพันที่สูงด้วยเช่นกัน
- แทงบอล 1×2 เป็นการเดิมพัน 3 แบบด้วยกัน การเดิมพันมีการแบ่งรูปแบบออกมาเป็น 1 ทีมเจ้าบ้านเป็นฝ่ายชนะ, X ทีมเจ้าบ้านเสมอกับทีมเยือน และ 2 เป็นการเดิมพันทีมเยือน ที่รับรองได้เลยว่าผู้เล่นจะสามารถเลือกเดิมพันได้ทุกลีกทั่วโลก ไม่ว่าจะเป็น ลีกบอลไทย และ ลีกบอลต่างประเทศ
- แทงบอลเตะมุม เป็นรูปแบบการเล่นเดิมพัน ที่นักเดิมพันต้องรวมแต้มบอลที่มีการเตะเข้ามุมทั้งหมดเตะมุม ซึ่งการเดิมพันเกมแทงบอลก็จะมีให้เลือกทั้ง ผลรวมแต้มบอลเตะมุมสูง และผลรวมแต้มบอลเตะมุมต่ำ มาพร้อมกับอัตราการจ่ายบอลเตะมุมอีกมากมาย
- แทงบอลแฮนดิแคป เป็นวิธีหนึ่งในการวางเดิมพันในการแข่งขันฟุตบอล ที่ผู้เล่นสามารถเลือกเดิมพันโดยใช้แต้มแฮนดิแคปเพื่อเพิ่มโอกาสในการชนะสำหรับทีมหรือผู้เล่นที่มีความเป็นอันดับต่ำกว่า หรือเพิ่มความท้าทายในการเดิมพันสำหรับทีมหรือผู้เล่นที่มีความเป็นอันดับสูงกว่า
ข้อได้เปรียบ เว็บพนันบอลออนไลน์ ไม่ผ่านเอเย่นต์
เมื่อพูดถึงเว็บพนันบอลออนไลน์ ไม่ผ่านเอเย่นต์ เราก็พบว่ามีความแตกต่างที่น่าสนใจเมื่อเปรียบเทียบกับเว็บพนันทั่วไปที่มักจะมีการใช้เอเย่นต์เป็นกลางในการแนะนำและให้บริการแก่ผู้เล่น ข้อได้เปรียบที่คุณสามารถรับรู้จากเว็บพนันบอลออนไลน์ ไม่ผ่านเอเย่นต์ ได้แก่:
ความเป็นส่วนตัวและความปลอดภัย
ความเป็นส่วนตัวและความปลอดภัยเป็นปัจจัยที่สำคัญอย่างยิ่งในการเล่นเว็บพนันบอลออนไลน์ที่เป็นเว็บตรงและไม่ผ่านเอเย่นต์ เหตุผลที่ความเป็นส่วนตัวเหล่านี้ถือเป็นคุณสมบัติที่สำคัญนักเพราะมีการให้ความสำคัญกับการรักษาความลับและความปลอดภัยของข้อมูลส่วนตัวของผู้ใช้งานอย่างสูงสุด ด้วยการใช้ระบบ SSL (Secure Sockets Layer) ตามมาตรฐานสากลที่ได้รับการยอมรับจากผู้ใช้งานทั่วโลก ทำให้ผู้เล่นมั่นใจได้ในเรื่องของความปลอดภัยของข้อมูลส่วนตัวของตนเอง
เมื่อคุณเล่นกับเว็บเหล่านี้ที่มีระบบความปลอดภัยและเป็นส่วนตัวที่มีคุณภาพสูง เราสามารถมั่นใจได้ว่าข้อมูลส่วนตัวของเราจะไม่ถูกเผยแพร่หรือนำไปใช้ในทางที่ไม่เหมาะสม ระบบ SSL ทำหน้าที่เข้ารหัสข้อมูลที่ถูกส่งระหว่างผู้ใช้งานและเซิร์ฟเวอร์ เพื่อป้องกันการถูกแอบแซบหรือการจับกุมข้อมูลส่วนตัว นอกจากนี้ เว็บพนันบอลที่เป็นเว็บตรงยังมีมาตรการความปลอดภัยอื่น ๆ อีกมากมาย เช่น ระบบการตรวจสอบความถูกต้องของบัญชีผู้ใช้งาน ระบบป้องกันการแอบแซบจากบุคคลที่ไม่ประสงค์ดี และการจัดการกับการฝากถอนเงินอย่างมีความปลอดภัย
การบริการลูกค้าที่ดี
การบริการลูกค้าที่ดี เป็นสิ่งสำคัญอย่างยิ่งสำหรับเว็บพนันที่ไม่ผ่านเอเย่นต์ เนื่องจากเป็นปัจจัยที่ส่งผลต่อประสบการณ์การเล่นและความพึงพอใจของผู้เล่น เว็บพนันเหล่านี้มักมุ่งหวังให้บริการลูกค้าที่ดีทั้งในเรื่องของการช่วยเหลือและการแก้ไขปัญหาอย่างมีมาตรฐานและรวดเร็ว
ผู้เล่นสามารถติดต่อทีมงานของเว็บพนันผ่านช่องทางต่าง ๆ เพื่อขอความช่วยเหลือในกรณีที่พบปัญหาหรือสงสัยเกี่ยวกับการเล่นหรือการทำธุรกรรมในเว็บไซต์นั้น รูปแบบการติดต่อมักมีหลายช่องทาง เช่น ทางอีเมล, แชทสด, หรือโทรศัพท์ โดยทีมงานการบริการลูกค้าจะพร้อมให้การช่วยเหลือและการแก้ไขปัญหาตลอด 24 ชั่วโมงตลอด 7 วัน ทำให้ผู้เล่นมั่นใจได้ว่าความช่วยเหลือจะมีการตอบสนองทันทีเมื่อต้องการ
โบนัสแทงบอลออนไลน์
โบนัสในการแทงบอลออนไลน์เป็นสิ่งที่เป็นที่นิยมและน่าตื่นตาตื่นใจสำหรับผู้เล่นที่สนใจทั้งการเดิมพันและโอกาสในการรับรางวัลเพิ่มเติม เว็บไซต์และแพลตฟอร์มการแทงบอลออนไลน์ต่างๆ มักจะมีโปรโมชั่นและโบนัสต่างๆ เพื่อดึงดูดผู้เล่นใหม่ และรักษาผู้เล่นที่มีอยู่แล้ว โดยบางครั้งโบนัสเหล่านี้อาจมาในรูปแบบต่างๆ ดังนี้:
- โบนัสต้อนรับ: โบนัสที่ได้รับเมื่อสมัครสมาชิกใหม่กับเว็บไซต์ ส่วนใหญ่จะเป็นเงินโบนัสหรือการจับคู่เงินฝากเป็นรางวัล เช่น โบนัส 100% ของยอดเงินฝากเริ่มต้น หรือโบนัสเงินฝากครั้งแรก เป็นต้น
- โบนัสฝากเงินเพิ่ม: เว็บไซต์อาจมีโปรโมชั่นที่ให้โบนัสเพิ่มเงินฝากในคราวหนึ่ง เช่น โบนัส 50% สำหรับการเติมเงินในวันที่กำหนด
- โบนัสแทงฟรี: โบนัสที่ให้เงินทุนในการเดิมพันในรูปแบบเงินสด โดยไม่ต้องเติมเงินเข้าบัญชีผู้ใช้งาน แต่มักมีเงื่อนไขในการถอนเงินสะสม
- โบนัสคืนเงิน: โบนัสที่ให้คืนเงินสำหรับการเสียเดิมพัน ในบางครั้งอาจเป็นรายสัปดาห์หรือรายเดือน
- โปรโมชั่นพิเศษ: โปรโมชั่นเฉพาะที่มีให้ในช่วงเวลาที่กำหนด เช่น ในช่วงการแข่งขันสำคัญ หรือเทศกาลต่างๆ
- โบนัสสะสมแต้ม: โบนัสที่มอบแต้มให้ในการเดิมพัน เมื่อสะสมถึงจำนวนที่กำหนด แล้วคุณสามารถแลกเป็นเงินหรือรางวัลอื่นๆได้
ผู้เล่นควรทำความเข้าใจในเงื่อนไขและข้อกำหนดของโบนัสที่เว็บไซต์กำหนด เพื่อป้องกันการเกิดความสับสนในการใช้งานและการถอนเงินสะสมที่ได้รับจากโบนัสนั้น โบนัสแทงบอลออนไลน์สามารถเพิ่มความสนุกและโอกาสในการชนะในการเดิมพันของคุณได้อย่างมีเสถียรภาพและมีประสิทธิภาพ
ความสะดวกสบายในการใช้งาน
ความสะดวกสบายในการใช้งานเป็นหนึ่งในคุณสมบัติ ที่ทำให้เว็บพนัน ไม่ผ่านเอเย่นต์นั้นเป็นที่นิยมและเป็นที่ต้องการของผู้เล่นหลายคน เว็บไซต์เหล่านี้มีความเข้าใจว่าประสบการณ์การเล่นที่ทำให้ผู้เล่นรู้สึกสบายใจและไม่มีความยุ่งยากจะเป็นสิ่งสำคัญอย่างยิ่ง ด้วยเหตุนี้ เว็บพนัน ไม่ผ่านเอเย่นต์ มักออกแบบเว็บไซต์ให้ใช้งานได้อย่างง่ายและสะดวกสบายอย่างเต็มที่
ไม่ว่าคุณจะเข้าเล่นผ่านคอมพิวเตอร์หรือมือถือ เว็บไซต์เหล่านี้ได้มีการออกแบบและปรับปรุงเพื่อให้สอดคล้องกับทุกอุปกรณ์และหน้าจอ ทำให้คุณสามารถเข้าถึงเกมพนันและบริการต่างๆ ได้อย่างรวดเร็วและไม่ต้องเสียเวลาในการปรับตัวเข้ากับแพลตฟอร์มต่างๆ ทั้งยังมีการจัดเรียงองค์ประกอบต่างๆ ให้เป็นระเบียบเรียบร้อย และมีขั้นตอนการใช้งานที่ชัดเจน เพื่อให้คุณสามารถทำรายการต่างๆ ได้อย่างง่ายดาย
อย่าลืมว่าการเลือกเว็บพนัน ไม่ผ่านเอเย่นต์ ที่เหมาะสมมีความสำคัญ เพื่อให้คุณเพลิดเพลินกับการเดิมพันอย่างปลอดภัยและเพลิดเพลินในความสนุกของการเล่นพนันบอลออนไลน์ได้อย่างมากขึ้น สามารถเลือกสมัครสมาชิกผ่านเว็บแทงบอลออนไลน์ ที่เราแนะนำผ่านบทความนี้ได้เลย
สรุปเกี่ยวกับเว็บแทงบอลออนไลน์
การเดิมพันกีฬาออนไลน์ไม่จำเป็นจะต้องเดินตามหาเจ้ามือเพื่อการเดิมพันอีกต่อไป เพราะสมัยนี้มีการให้บริการเว็บแทงบอลออนไลน์กันเป็นจำนวนมาก และสามารถเล่นได้เลยโดยไม่ต้องรอให้เจ้ามือเปิดรับ อีกทั้งเว็บไซต์เหล่านี้ยังมีอัตราเดิมพันที่ค่อนข้างเป็นธรรม โดยเฉพาะอย่างยิ่งเว็บที่ให้บริการผ่านค่ายเกมชั้นนำต่าง ๆ
อย่างไรก็ตาม การมองหาเว็บไซต์เหล่านี้ในการใช้งานนั้นอาจเป็นเรื่องที่ต้องใช้เวลา ดังนั้นแล้วคุณสามารถทำการมองหารีวิวจากผู้เชี่ยวชาญที่ทดลองใช้งานจริง หรือบทความที่น่าเชื่อถือก่อนทำการตัดสินใจ ยกตัวอย่างเช่นการรีวิวจากพวกเขาในข้างต้น เพื่อให้แน่ใจว่าจะได้ใช้บริการเว็บไซต์ที่ปลอดภัยและได้มาตรฐาน และมีการจ่ายเงินจริง
คำถามที่พบบ่อย
เว็บแทงบอลออนไลน์ คืออะไร?
เว็บแทงบอลออนไลน์เป็นแพลตฟอร์ม ที่ให้ผู้เล่นทำการเดิมพันหรือแทงเงินในการแข่งขันฟุตบอลผ่านอินเทอร์เน็ต ผู้เล่นสามารถวางเดิมพันในผลการแข่งขัน คะแนน, ทีมที่ชนะ, การลงโทษและอื่นๆ ได้ตามต้องการ โดยทั่วไปแล้วเว็บเหล่านี้จะมีราคาต่อรองที่แตกต่างกันและส่วนลดให้กับผู้เล่นในบางครั้ง
เว็บแทงบอลมีความปลอดภัย หรือไม่?
ความปลอดภัยของเว็บแทงบอลออนไลน์ขึ้นอยู่กับเว็บไซต์เฉพาะ มีเว็บที่มีความน่าเชื่อถือและมีการรักษาข้อมูลส่วนตัวของผู้เล่นอย่างเหมาะสม แต่ก็มีเว็บที่ไม่น่าเชื่อถือที่อาจเกิดปัญหาด้านความปลอดภัยได้ การค้นคว้าและอ่านรีวิวเกี่ยวกับเว็บที่สนใจเป็นสิ่งสำคัญเพื่อป้องกันการเสี่ยงภัยที่ไม่จำเป็น
วิธีฝากเงินและถอนเงิน เว็บแทงบอลออนไลน์ มีอย่างไรบ้าง?
เว็บแทงบอลออนไลน์มักมีวิธีฝากเงินและถอนเงินหลากหลาย เช่น โอนเงินผ่านธนาคาร, บัตรเครดิต, บัตรเดบิต, พรีเพย์การ์ด และบางทีอาจมีวิธีการอื่นๆ ที่สะดวกสบายในการทำธุรกรรม เมื่อถึงการถอนเงินก็จะมีขั้นตอนที่ผู้เล่นต้องปฏิบัติตาม ซึ่งอาจรวมถึงการยืนยันตัวตนและสำเนาเอกสารสำคัญเพื่อป้องกันการฟอกเงินและการประพฤติมิชอบ